Paytm CEO Unveils Shocking Truth: ‘The Power of Password Length’ in Defeating Hackers

Paytm CEO Unveils Shocking Truth: ‘The Power of Password Length’ in Defeating Hackers
In a world where our digital lives are increasingly intertwined with online platforms and services, security has become paramount. Passwords are the frontline defense, the virtual keys to our private and sensitive information. But how secure are our passwords, and what makes them formidable barriers against hacking attempts? Paytm CEO Vijay Shekhar Sharma recently shed light on this crucial aspect of online security in a startling revelation: the real power in defeating hackers lies in the length of your password, not just its complexity.
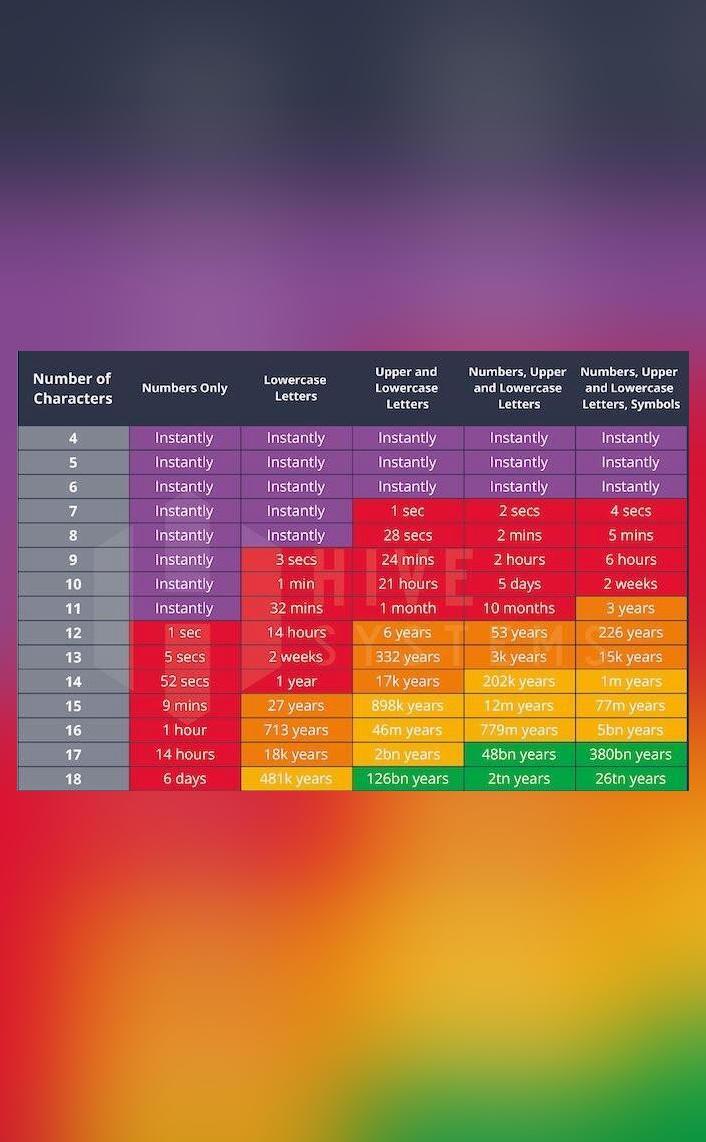
Vijay Shekhar Sharma, a visionary leader in India’s digital payment and financial technology sector, took to social media to share a picture that speaks volumes about the time it takes for hackers to crack passwords. The message was clear: our passwords are only as strong as their length allows them to be.
The image Sharma shared highlights a fundamental flaw in many people’s approach to online security. It demonstrates that even passwords comprising numbers, lowercase and uppercase letters, and symbols can be cracked almost instantly if they are short – specifically, if they are up to 6 characters long.
In an era where cyberattacks and data breaches are on the rise, and hackers continue to develop increasingly sophisticated techniques, the importance of strong, resilient passwords cannot be overstated. However, the traditional wisdom has often focused on the complexity of passwords, with experts advising users to create intricate combinations of characters. Vijay Shekhar Sharma’s revelation challenges this conventional thinking and emphasizes the significance of password length as the linchpin of robust security.
When it comes to password strength, the common understanding is that a complex, alphanumeric, and symbol-rich combination is enough to thwart most hacking attempts. Users are frequently encouraged to include uppercase letters, lowercase letters, numbers, and special symbols in their passwords. While this is undoubtedly a valuable practice, Sharma’s message highlights the fact that the key factor in determining a password’s strength is its length.
In an age when hacking tools and techniques continue to evolve and become more sophisticated, even the most intricate passwords can be cracked if they lack sufficient length. Hackers employ various methods to decipher passwords, including dictionary attacks, brute force attacks, and rainbow tables. These attacks can be significantly accelerated when dealing with short passwords, making it essential to prioritize the length of a password to enhance security.
A brute force attack is a type of hacking attempt in which a malicious actor systematically tries every possible combination of characters until the correct password is found. Short passwords are more vulnerable to brute force attacks because there are fewer possible combinations to guess. In contrast, longer passwords require an exponentially greater number of attempts to crack, making them significantly more robust against these attacks.
The revelation by Paytm’s CEO reinforces the importance of adopting longer passwords as a security measure. By extending the length of your password, you significantly increase the time and effort required for a hacker to break into your account. This additional time can be the difference between a secure account and a compromised one.
The significance of password length can be better understood through a practical example. Consider two passwords: “P@ssw0” and “MySecurePassword2023!” The first, “P@ssw0,” is a common choice for many users because it includes uppercase and lowercase letters, numbers, and a symbol. It may seem strong at first glance, but it’s only six characters long. On the other hand, “MySecurePassword2023!” is a longer password with 18 characters, encompassing a mix of uppercase letters, lowercase letters, numbers, and symbols. Despite the apparent complexity of the first password, the longer password provides significantly stronger security.
If we compare the two passwords against a brute force attack, the difference becomes evident. A hacker would need a considerable amount of time to crack the longer password, while the shorter password could be compromised almost instantaneously. This example highlights the vital role that password length plays in protecting your online accounts and sensitive information.
Vijay Shekhar Sharma’s message aligns with the recommendations of cybersecurity experts worldwide. As hacking techniques become more advanced and efficient, it’s essential to adopt a multi-faceted approach to online security. While complexity in password creation is vital, Sharma’s revelation underscores that it’s only part of the equation.

Here are some essential guidelines for creating robust passwords:
1. Length Matters: Prioritize length when creating passwords. Aim for a minimum of 12-16 characters, or even longer when possible. Longer passwords exponentially increase the time required to crack them.
2. Avoid Common Words and Phrases: Refrain from using easily guessable words, phrases, or patterns, such as “password,” “123456,” or “qwerty.” These are often the first combinations attempted by hackers.
3. Mix Character Types: Create passwords that include a mix of uppercase and lowercase letters, numbers, and special symbols. This adds an extra layer of complexity to your password.
4. Unique for Each Account: Use different passwords for each of your online accounts. Reusing passwords across multiple platforms can lead to catastrophic security breaches if one of them is compromised.
5. Consider Passphrases: Instead of using a single word or short combination, consider using a passphrase – a series of random words or a sentence that only makes sense to you. Passphrases can be both long and memorable.
6. Enable Two-Factor Authentication (2FA): Whenever possible, enable 2FA for your online accounts. This adds an additional layer of security, making it significantly more challenging for hackers to gain access to your account.
7. Password Managers: Consider using a reputable password manager to generate, store, and autofill complex and unique passwords for each of your accounts. This simplifies the process of managing secure passwords.
Vijay Shekhar Sharma’s insightful revelation serves as a wake-up call for individuals and organizations alike. It highlights the critical need to shift the focus from merely creating complex passwords to prioritizing the length of those passwords. As cyber threats continue to grow in sophistication, understanding and implementing this fundamental aspect of online security can make a substantial difference in safeguarding our digital lives.
Experts in the field of cybersecurity have lauded Sharma’s message, underlining its importance in creating a more secure online environment. The CEO’s proactive stance on educating the public about password security demonstrates the responsibility that business leaders and organizations have in promoting a safer digital ecosystem.

While the onus of securing our online accounts lies with individual users, organizations must also play their part in ensuring robust security measures. This includes implementing stringent password policies, regularly educating employees and users on best practices, and investing in advanced security technologies to protect user data.
In conclusion, the power of password length in defeating hackers cannot be overstated. In a time when online security is paramount, Vijay Shekhar Sharma’s revelation serves as a potent reminder that longer passwords are the linchpin of robust security. As we navigate the digital landscape, it’s imperative that we prioritize not only the complexity but also the length of our passwords, thereby bolstering our defenses against the ever-evolving threats of the cyber world.




